Discover Loop Iteration in Python | Lesson 6
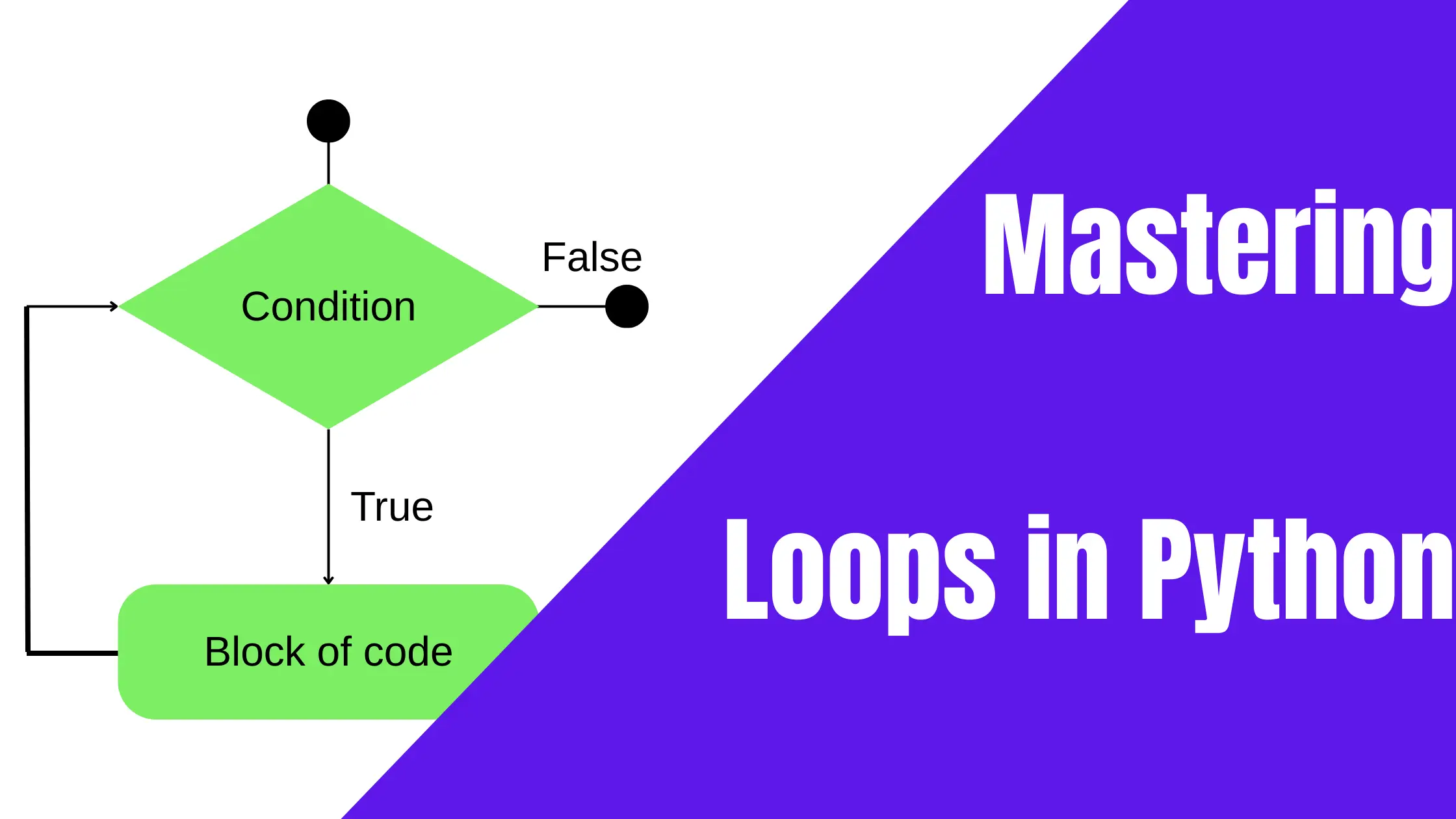
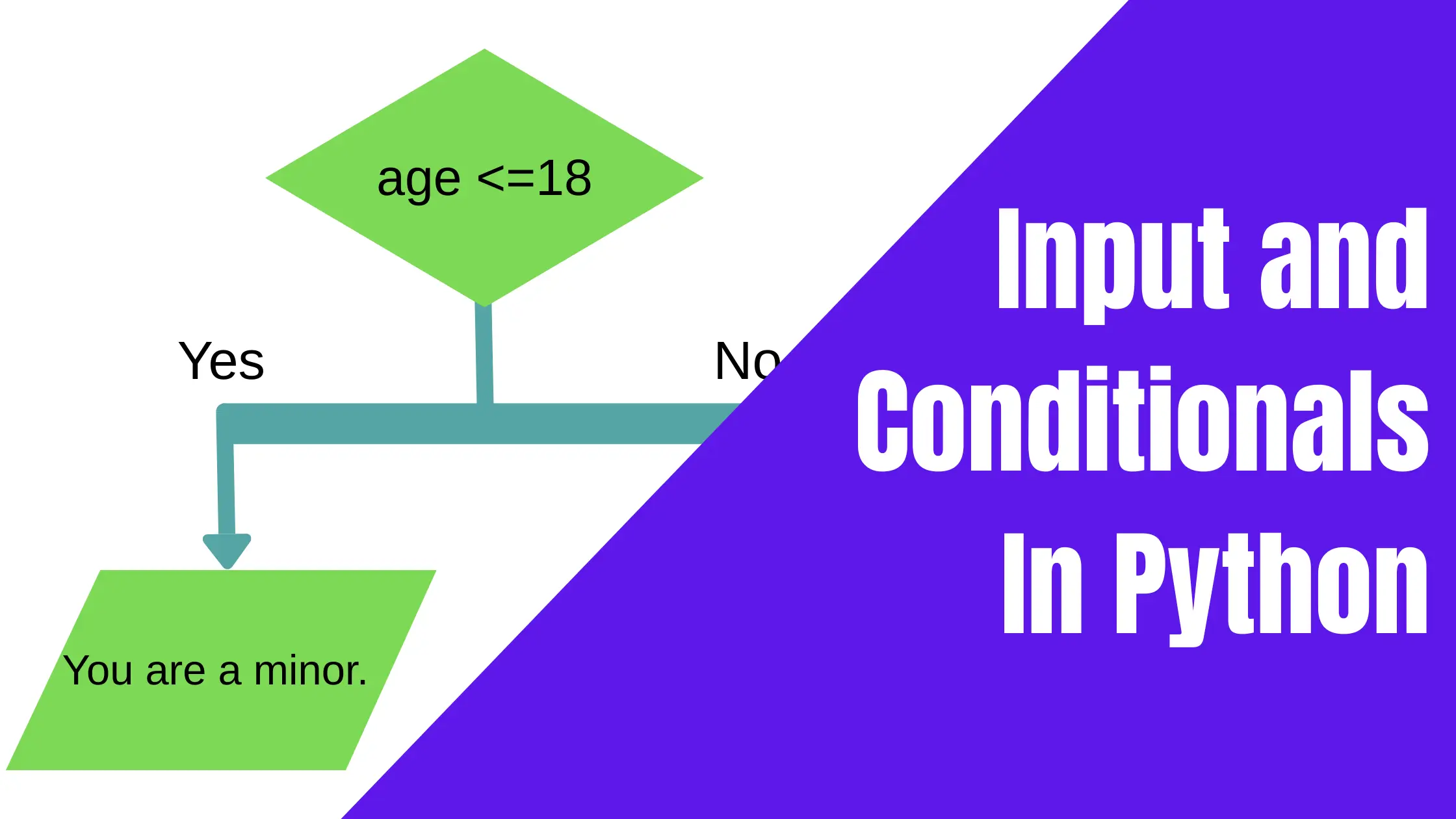
Loops are a crucial part of programming, and understanding loop iteration is essential for becoming an expert programmer. For clarity, loops allow you to execute a block of code repeatedly without having to write the same code multiple times. If you have not used loops before, be sure to explore mastering loops in Python. Keep reading … Read more
 Skip to content
Skip to content